The device mapper is a framework provided by the Linux kernel for mapping physical block devices onto higher-level virtual block devices. It forms the foundation of the logical volume manager (LVM), software RAIDs and dm-crypt disk encryption, and offers additional features such as file system snapshots.[1]
Device mapper works by passing data from a virtual block device, which is provided by the device mapper itself, to another block device. Data can be also modified in transition, which is performed, for example, in the case of device mapper providing disk encryption or simulation of unreliable hardware behavior.
This article focuses on the device mapper implementation in the Linux kernel, but the device mapper functionality is also available in both NetBSD and DragonFly BSD.[2][3]
Usage
Applications (like LVM2 and Enterprise Volume Management System (EVMS)) that need to create new mapped devices talk to the device mapper via the libdevmapper.so shared library, which in turn issues ioctls to the /dev/mapper/control device node.[4] Configuration of the device mapper can be also examined and configured interactively—or from shell scripts—by using the utility.[5][6]
Both of these two userspace components have their source code maintained alongside the LVM2 source.[7]
Features
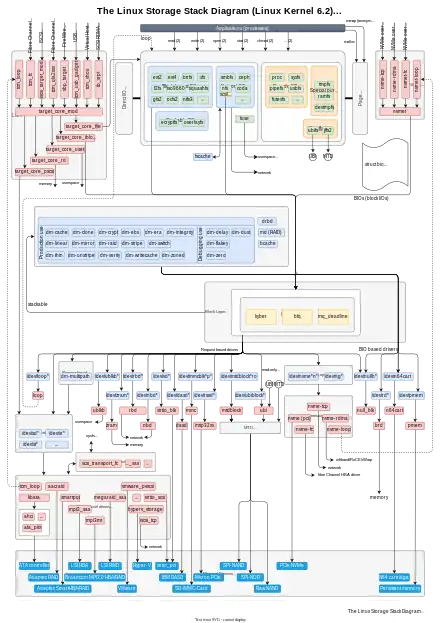
Functions provided by the device mapper include linear, striped and error mappings, as well as crypt and multipath targets. For example, two disks may be concatenated into one logical volume with a pair of linear mappings, one for each disk. As another example, crypt target encrypts the data passing through the specified device, by using the Linux kernel's Crypto API.[1]
As of 2014, the following mapping targets are available:[1][5]
- cache – allows creation of hybrid volumes, by using solid-state drives (SSDs) as caches for hard disk drives (HDDs)
- clone – will permit usage before a transfer is complete.
- crypt – provides data encryption, by using the Linux kernel's Crypto API
- delay – delays reads and/or writes to different devices (used for testing)
- era – behaves in a way similar to the linear target, while it keeps track of blocks that were written to within a user-defined period of time[9]
- error – simulates I/O errors for all mapped blocks (used for testing)
- flakey – simulates periodic unreliable behaviour (used for testing)
- linear – maps a continuous range of blocks onto another block device
- mirror – maps a mirrored logical device, while providing data redundancy
- multipath – supports the mapping of multipathed devices, through usage of their path groups
- raid – offers an interface to the Linux kernel's software RAID driver (md)
- snapshot and snapshot-origin – used for creation of LVM snapshots, as part of the underlying copy-on-write scheme
- striped – stripes the data across physical devices, with the number of stripes and the striping chunk size as parameters
- thin – allows creation of devices larger than the underlying physical device, physical space is allocated only when written to
- zero – an equivalent of
/dev/zero, all reads return blocks of zeros, and writes are discarded
Applications
Linux kernel features and projects built on top of the device mapper include the following:
- cryptsetup – utility used to conveniently setup disk encryption based on dm-crypt
- dm-crypt/LUKS – mapping target that provides volume encryption
- dm-cache – mapping target that allows creation of hybrid volumes
- dm-integrity – mapping target that provides data integrity, either using checksumming or cryptographic verification,[10][11] also used with LUKS[12]
- dm-log-writes – mapping target that uses two devices, passing through the first device and logging the write operations performed to it on the second device[13]
- dm-verity – validates the data blocks contained in a file system against a list of cryptographic hash values, developed as part of the ChromiumOS project[14]
- – provides access to "fake" RAID configurations via the device mapper
- DM Multipath – provides I/O failover and load-balancing of block devices within the Linux kernel
- Docker – uses device mapper to create copy-on-write storage for software containers
- DRBD (Distributed Replicated Block Device)
- EVMS (deprecated)
- – utility called from hotplug upon device maps creation and deletion
- LVM2 – logical volume manager for the Linux kernel
- VeraCrypt - Linux version of TrueCrypt
- VDO - Virtual Data Optimizer
References
- 1 2 3 "Logical Volume Manager Administration, Appendix A. The Device Mapper". Red Hat. Retrieved 2013-09-29.
- ↑ "NetBSD Kernel Interfaces Manual: dm(4)". netbsd.gw.com. 2008-08-30. Retrieved 2015-01-25.
- ↑ "DragonFly On-Line Manual Pages: dm(4)". dragonflybsd.org. 2010-07-28. Retrieved 2014-06-06.
- ↑ "libdevmapper.h". sourceware.org. Retrieved 2013-09-29.
- 1 2 "dmsetup(8) - Linux man page". man.cx. Retrieved 2013-10-22.
- ↑ "Logical Volume Manager Administration". Appendix A.2. The dmsetup Command. Red Hat. Retrieved 2013-09-29.
- ↑ "Device-mapper Resource Page". sourceware.org. Retrieved 2013-09-29.
- ↑ Werner Fischer; Georg Schönberger (2015-06-01). "Linux Storage Stack Diagram". Thomas-Krenn.AG. Retrieved 2015-06-08.
- ↑ "6. Block layer". Linux kernel 3.15. kernelnewbies.org. 2014-06-08. Retrieved 2014-06-15.
- ↑ "dm-integrity". cryptosetup project. 2018-04-30. Retrieved 2018-05-08.
- ↑ "dm-integrity target". kernel.org. 2017-05-13. Retrieved 2018-05-08.
- ↑ "cryptsetup - manage plain dm-crypt and LUKS encrypted volumes". 2018-01-01. Retrieved 2018-05-08.
- ↑ "Linux kernel documentation: Documentation/device-mapper/log-writes.txt". kernel.org. 2015-05-29. Retrieved 2015-10-13.
- ↑ Jonathan Corbet (2011-09-19). "dm-verity". LWN.net. Retrieved 2015-10-13.
External links
- Device mapper home at Red Hat Archived 2006-03-15 at the Wayback Machine
- "Right To Your Own Devices". Linux Gazette. May 2005. – an article illustrating the use of various device mapper targets
- userspace tool to set up software RAID using various RAID metadata formats
- Multipath support in the device mapper, LWN.net, February 23, 2005, by Jonathan Corbet