In September 2022, Optus, Australia's third-largest telecommunications company, suffered a data breach, affecting up to 10 million current and former customers, over a third of Australia's population. Information illegally obtained included names, birthdates, home addresses, phone numbers, email contacts, and passport and driving licence numbers. Conflicting claims have been made about how the breach happened; Optus presented it as a complicated attack on their systems, while an Optus insider and the Australian government have claimed that a human error causing a vulnerability in the company's API occurred. A ransom notice was made, asking for A$1,500,000 to stop the data being sold online. After a few hours, they deleted the ransom notice and apologised for their actions.
Optus has received criticism from government figures, including Home Affairs and Cyber Security Minister Clare O'Neil and Minister for Government Services Bill Shorten, for their role in the attack and for being uncooperative with government agencies and the general public. The government has announced legislation, including allowing information to be shared with financial services and Government agencies, and reforms to Australia's security of critical infrastructure laws, to help the government act for future breaches.[1]
In response to the breach, Optus has agreed to pay for the replacements of passports that have been compromised, commissioned an external review, and given highly affected customers a subscription to a credit monitoring service. Optus has also apologised for the breach. Optus has faced criticism from customers for not being responsive and providing inadequate responses to customers affected. Multiple investigations into the breach and a class-action lawsuit from affected customers are ongoing as of June 2023.
Background
Optus is an Australian telecommunications company, founded in 1981 with the formation of the government-owned AUSSAT, specialising in satellites.[2] AUSSAT was then privatised in 1991 to a consortium of businesses including Mayne Nickless and AMP Limited.[3] Optus is Australia's third-largest telecommunications company, holding a 13.1% market share.[4] At the time of the breach, Optus had around 10 million customers, well over a third of Australia's population of around 26.64 million.[5][6]
Breach
On 20 September, Optus's technical team noticed and investigated suspicious activity on its network. The next day, it was identified that Optus's systems had sustained a data breach, and regulators were informed. On 22 September, the company went public with the data breach, informing news agencies.[5][7] Optus recommended that people increase attention to potential fraudulent activity, but stated that they did not know if the breach had caused any harm to customers. At this point, Optus did not state how many customers were affected, nor if the data taken had caused harm.[8] Information illegally obtained included names, birthdates, home addresses, phone numbers, email contacts, and passport and driving licence numbers.[5]
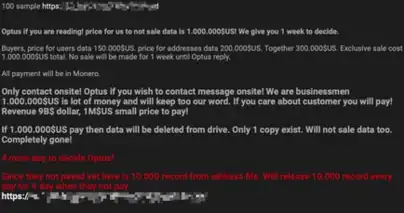
On 23 September, Optus denied claims made by an insider that a mistake had occurred where Optus's API had accidentally been left exposed to a test network that had internet access. They instead claimed a complicated breach had occurred, and that the company had a strong cybersecurity system.[9] The Australian Broadcasting Corporation was told that Optus believed the hacker had scraped the company's consumer database, with only a third of the total data in the database copied and extracted.[9]
On 24 September, Optus and the Australian Federal Police (AFP), now having opened a criminal investigation, received reports that data from the leak was being sold online, and were monitoring the dark web for any attempt of selling data online.[10] The same day, a user on BreachForums posted a ransom note believed to be legitimate by some cybersecurity experts but unconfirmed by Optus and the AFP, demanding that Optus pay $1,500,000 in privacy-focused cryptocurrency Monero. They said that they would release the personal information of 10,000 customers every day that Optus did not pay the ransom until a week elapsed, with a sample of the information of 200 customers. After the week elapsed, they were to sell the data for A$400,000 to anyone who wants it.[11] After a few hours, the user deleted their original post and appeared to apologise for their actions despite no ransom being paid, stating that it was a "mistake to scrape publish [sic] data in first place"[11] and that there were too many people paying attention to the breach. The user noted that they would have reported the exploit that they used if they had the ability to contact Optus, noting the lack of a secure mail/messaging contact or bug bounties.[11]
Government response
Home Affairs and Cyber Security Minister Clare O'Neil alleged that Optus was at fault for the attack, refuting Optus's argument that the attack was complicated. O'Neil also stated that the attack should not have happened, stating: "Responsibility for the security breach rests with Optus[,] and I want to note that the breach is of a nature that we should not expect to see in a large telecommunications provider in this country".[12]
The federal government announced emergency regulation on 6 October so that drivers licences, Medicare information and passport numbers can be temporarily shared with financial services, the Commonwealth, and state or territory agencies to assist with monitoring the accounts of customers affected by the breach for potential scams or fraud. Financial institutions will have to commit to several actions to receive the data, including honouring privacy obligations and deleting data once it has been used. The Council of Financial Regulators have also been asked to identify and report on changes for financial instructions to identify customers who are at risk of scams and fraud. The changes will be in place for 12 months. Treasurer Jim Chalmers stated that the measures will help protect customers from scams, and to detect fraud.[13]
O'Neil expressed frustration at the lack of ability for the government to intervene in the data breach, with the government being unable to assist with the clean-up following the breach, or compel Optus to give government services information. She stated that Australian law had no use for the government when needed, as Australia's security of critical infrastructure laws only allowed the government to legally intervene while a data breach was occurring.[14]
Several new security measures have been announced following the breach to protect victims from fraud, including banks being informed of data breaches faster to prevent the use of data to fraudulently access bank accounts.[15] The federal government has also flagged an overhaul of the $1.7 billion cybersecurity plan introduced by the previous government, including additional powers for the government to intervene regarding cybersecurity. The government is also considering a Cyber Security Act to create standards and obligations for industry and government, and a reform to the Security of Critical Infrastructure Act to bring customer data and systems under the definition of "critical infrastructure" allowing the government to intervene in major data breaches.[16]
In April 2023, the National Office of Cyber Security was founded, albeit with 5 full-time staff members and no additional funding than what was already given to the Department of Home Affairs.[17] In June 2023, Air Marshal Darren Goldie was appointed as Australia's inaugural Cyber Security Coordinator.[18] In November 2023, Goldie was recalled to the Department of Defence regarding a workplace matter, with cyber and infrastructure security head Hamish Hansford to take on the position in the interim.[19]
On 27 February 2023, Prime Minister Anthony Albanese and O'Neil hosted a roundtable with industry and civil society groups on cybersecurity following the data breach. A discussion paper was released regarding the role of the federal government in increasing Australia's cybersecurity capability.[16][20]
The state governments of Queensland, Victoria, South Australia and Western Australia have agreed to pay for the replacement of driver's licenses for people that had their driver's license number compromised by the breach.[21][22] In Victoria, plans to add a second number to driver's licenses was fast-tracked, with all victims of the breach receiving the second number as part of their replacements, with the intention of protecting Victorians from identity theft.[23]
Optus response

On the day that the breach was announced, Optus set up a "war room" to deal with the breach at its headquarters in Macquarie Park. This involved around 150 employees and was headed by former Premier of New South Wales Gladys Berejiklian and regulatory and public affairs head Andrew Sheridan.[24]
Optus commissioned Deloitte to do an "independent external review" regarding the breach.[25] Optus also signed up its "most affected" customers to get a 12-month subscription to credit monitoring service Equifax Protect after O'Neil requested the company buy credit monitoring for its customers in Question Time.[26] Optus CEO Kelly Bayer Rosmarin deeply apologised for the attack on behalf of the company.[27] Optus has put aside $140 million for costs relating to the breach, including to replace hacked identification documents, the Equifax Protect subscriptions and the Deloitte review.[27] Optus has promised to pay for the replacement of Australian and foreign passports that have been compromised in the breach.[28]
Optus reported that 2.1 million of its customers had had identity documents stolen as part of the hack. Of these, 1.2 million customers, according to Optus, had at least one current, valid number from a form of personal identification stolen. The remaining 900,000 customers had expired identity numbers stolen.[29]
Allegations of a lack of communication from Optus have been made by Services Australia. On 27 September, Services Australia wrote to Optus “asking for the full details of all affected customers with Services Australia credentials exposed, such as Medicare cards and/or Centrelink concession cards”.[14] Minister for Government Services Bill Shorten stated that, a week later, Services Australia had not received any data from Optus. Optus claimed that they were "in contact with Services Australia and we will be letting all affected customers know the guidance on the steps they can take".[14] There was also confusion regarding the number of Medicare ID numbers stolen, with Shorten telling a press conference that around 36,900 ID numbers had been stolen, and Optus identifying that 14,900 ID numbers had been stolen.[14]
Customers have also reported issues regarding communicating with the company. Customers stated that Optus could not confirm if their personal information was part of the data breach after contacting them several times, the company's chatbot failing to understand questions from customers about the breach, poor responses from sales representatives, not receiving a response from Optus at all, and delays in warning customers regarding compromises of personal information. A customer stated that, "Ultimately, we are sitting ducks for identity theft, and given that we can’t change our dates of birth, address or names, there isn’t much we can do about it, which is incredibly frustrating".[26]
On 8 March 2023, Bayer Rosmarin restated Optus's claim that the attack was sophisticated, stating at a business summit that “The skilled criminal had knowledge of Optus’ systems and cycled through many tens of thousands of internet protocol addresses in an attempt to evade our automated cyber monitoring”.[30] She also stated that Optus never paid a ransom to the hacker, and that the primary reason for the breach was for other scam purposes.[30]
In November 2023, Bayer Rosmarin resigned as CEO of Optus after the 2023 Optus outage following mounting pressure to resign due to the outage and the date breach.[31]
Legal action
On 6 October, a 19-year-old Sydney man, Dennis Su, was arrested by the AFP in his home at Rockdale for blackmailing 93 Optus customers affected by the breach. He claimed that he would commit financial crimes using their personal data unless they paid A$2000 to him, which none did. He was charged with a count of using a telecommunication network with intent to commit a serious offence and a count of dealing with identification information with intent to commit an offence. AFP Assistant Commissioner Justine Gough stated that he was not suspected of being responsible for the breach, and warned people to not click on links claiming to be from Optus.[32] Su pleaded guilty in November 2022. He did not go to jail due to a guilty pleading, his age and showing remorse for his actions, instead receiving an 18-month community corrections order.[33]
The Office of the Australian Information Commissioner (OAIC) has launched an investigation into the breach, concerning Optus's handling of the personal data of customers, focusing on whether Optus took reasonable steps to protect consumers affected by the breach from fraud, misuse, or loss, and whether the information collected was necessary for Optus to keep. Australian Communications and Media Authority is also investigating the breach, focusing on whether Optus breached its obligations regarding the protection and disposal of personal data.[34] OAIC was given $5.5 million to investigate the breach over two years by the federal government in its October 2022 budget.[25]
A class action has been launched by law firm Slater & Gordon, alleging Optus "breached laws and its own policies by failing to adequately protect customer data and destroy or de-identify former customer data". The ongoing class action has been joined by 100,000 current and former customers, wanting compensation for losses, including the time to replace identification documents, and the stress caused. Optus has stated it will defend its actions.[35][36] In court, Slater & Gordon lawyers requested that the Deloitte report be released to the public, arguing that it could reveal the possible causes for the data breach. Optus declined to do so, despite Bayer Rosmarin stating in March 2023 that Optus would release "share key recommendations and learnings"[37] from the report.[37][38]
See also
References
- ↑ Crozier, Ry (2022-10-01). "Australian police, banks join forces to monitor leaked Optus dataset". itnews. Archived from the original on 2022-09-30. Retrieved 2023-10-17.
- ↑ "LOWDOWN - Australia's History in Satellite Technology". web.archive.org. 2007-06-08. Retrieved 2024-01-03.
- ↑ "OPTUS CHOSEN TO TAKE ON TELECOM". Australian Financial Review. 1991-11-20. Retrieved 2024-01-03.
- ↑ Bradstock, Emma (2022-08-18). "Largest Internet Providers In Australia | Plans & Prices". Canstar Blue. Archived from the original on 2023-06-10. Retrieved 2023-06-10.
- 1 2 3 Turnbull, Tiffanie (2022-09-29). "Optus: How a massive data breach has exposed Australia". BBC News. Archived from the original on 2023-05-16. Retrieved 2023-05-16.
- ↑ "National, state and territory population, June 2023 | Australian Bureau of Statistics". www.abs.gov.au. 2023-12-14. Retrieved 2024-01-03.
- ↑ Smith, Paul (2022-12-21). "Inside the Optus hack that woke up Australia". Australian Financial Review. Archived from the original on 2023-05-20. Retrieved 2023-05-20.
- ↑ McElroy, Nicholas (2022-09-22). "Optus says customer information compromised in cyber attack". ABC News. Archived from the original on 2022-09-23. Retrieved 2023-05-16.
- 1 2 "Optus rejects insider claims of 'human error' as possible factor in hack affecting millions of Australians". ABC News. 2022-09-23. Archived from the original on 2022-09-24. Retrieved 2023-05-16.
- ↑ Belot, Henry (2022-09-24). "AFP monitoring dark web amid allegations stolen Optus data may be sold online". ABC News. Archived from the original on 2023-05-18. Retrieved 2023-05-16.
- 1 2 3 "An alleged hacker has offered their 'deepest apologies' to Optus. Here's the latest on the data breach". ABC News. 2022-09-27. Archived from the original on 2022-10-03. Retrieved 2023-05-16.
- ↑ Evans, Jake (2022-09-26). "Home affairs minister says Optus 'left window open' for cyber criminals". ABC News. Archived from the original on 2022-09-27. Retrieved 2023-05-16.
- ↑ Evans, Jake (2022-10-06). "Optus given temporary power to share compromised data with banks following hack". ABC News. Archived from the original on 2022-10-09. Retrieved 2023-05-17.
- 1 2 3 4 Crozier, Ry. "Services Australia struggles to gauge exposure to Optus data breach". iTnews. Archived from the original on 2023-05-18. Retrieved 2023-05-18.
- ↑ Speers, David; Greene, Andrew (2022-09-28). "Federal government to unveil new security measures following massive Optus data breach". ABC News. Archived from the original on 2023-05-17. Retrieved 2023-05-17.
- 1 2 Evans, Jake (2023-02-26). "Federal government to rewrite cyber laws after Optus, Medibank hacks". ABC News. Archived from the original on 2023-05-17. Retrieved 2023-05-17.
- ↑ "Govt fires up National Cyber Security Office". Information Age. Retrieved 2024-01-03.
- ↑ ACSM Admin (2023-06-23). "Australia's New National Cyber Security Coordinator - Australian Cyber Security Magazine". Retrieved 2024-01-03.
- ↑ Bajkowski, Julian (2023-11-15). "O'Neil's National Cybersecurity Coordinator sent back to Defence". The Mandarin. Retrieved 2024-01-03.
- ↑ Foster, Jeffrey (2023-02-28). "Australia has a new cybersecurity agenda. Two key questions lie at its heart". The Conversation. Archived from the original on 2023-05-19. Retrieved 2023-05-19.
- ↑ "Optus data breach: What to do about replacing your driver's licence and passport". SBS News. Archived from the original on 2023-05-20. Retrieved 2023-05-20.
- ↑ Cowie, Tom (2022-10-29). "VicRoads to issue almost 1 million free driver's licences after Optus hack". The Age. Archived from the original on 2023-05-20. Retrieved 2023-05-20.
- ↑ Cowie, Tom (2022-10-29). "VicRoads to issue almost 1 million free driver's licences after Optus hack". The Age. Archived from the original on 2023-06-03. Retrieved 2023-06-15.
- ↑ Smith, Paul (2022-12-21). "Inside the Optus hack that woke up Australia". Australian Financial Review. Archived from the original on 2023-05-20. Retrieved 2023-05-20.
- 1 2 Branco, Jorge (2022-10-26). "Privacy watchdog given $5.5 million to investigate Optus cyber breach". www.9news.com.au. Archived from the original on 2023-05-18. Retrieved 2023-05-18.
- 1 2 Taylor, Josh (2022-09-26). "Optus customers exasperated by chatbots and 'rubbish' communication after data breach". The Guardian. ISSN 0261-3077. Archived from the original on 2023-05-18. Retrieved 2023-05-18.
- 1 2 Samios, Zoe (2022-11-10). "Optus hack to cost at least $140 million". The Sydney Morning Herald. Archived from the original on 2022-11-13. Retrieved 2023-05-18.
- ↑ Conifer, Dan; Xiao, Alison; Bogle, Ariel (2022-11-03). "Optus promises to pay cost of replacing foreign passports compromised in data breach". ABC News. Archived from the original on 2022-11-03. Retrieved 2023-05-20.
- ↑ Crozier, Ry. "Deloitte brought in to examine Optus data breach". iTnews. Archived from the original on 2023-05-18. Retrieved 2023-05-18.
- 1 2 Muroi, Millie (2023-03-08). "Optus boss says 'skilled criminal' behind cyberattack, admits telco lost customers". The Sydney Morning Herald. Archived from the original on 2023-05-20. Retrieved 2023-05-20.
- ↑ Swan, David (2023-11-20). "Optus CEO Kelly Bayer Rosmarin resigns". The Sydney Morning Herald. Retrieved 2024-01-03.
- ↑ Lapham, Jake (2022-10-06). "Sydney teen demanded $2,000 from Optus customers as part of data breach scam, AFP says". ABC News. Archived from the original on 2022-10-06. Retrieved 2023-05-17.
- ↑ "Sydney man avoids jail over scam texts using Optus hack data". www.9news.com.au. 2023-02-07. Archived from the original on 2023-05-20. Retrieved 2023-05-20.
- ↑ Borys, Stephanie (2022-10-11). "Optus facing new probes over data hack, could be forced to pay millions in compensation". ABC News. Archived from the original on 2022-10-13. Retrieved 2023-05-17.
- ↑ Jackson, Lewis (2023-04-21). Osterman, Cynthia (ed.). "Australia's Optus hit with class action over cybersecurity breach". Reuters. Archived from the original on 2023-05-17. Retrieved 2023-05-17.
- ↑ Bonyhady, Nick; Abbott, Lachlan (2023-04-20). "Class action lawsuit launched against Optus after devastating hack". The Sydney Morning Herald. Archived from the original on 2023-05-20. Retrieved 2023-05-20.
- 1 2 Baird, Lucas (2023-03-08). "'No victims' of Optus data hack: CEO". Australian Financial Review. Retrieved 2023-10-04.
- ↑ Tarabay, Jamie (2023-09-20). "Massive Australian Ransomware Attack Has Victims Demanding Answers". Bloomberg.com. Retrieved 2023-10-04.